Brave blocks CNAME tracking, what about Vivaldi?
-
So this is circulating the news for a month now,
https://www.theregister.com/2020/10/28/brave_cname_block/ ,
https://www.ghacks.net/2020/11/17/brave-browser-gets-cname-based-adblocking-support/, but we don't have a thread here.
It's the old (sad) story about cursed Google's API and how uBlock could block it only in Firefox, and not always successfully: https://blog.apnic.net/2020/08/04/characterizing-cname-cloaking-based-tracking/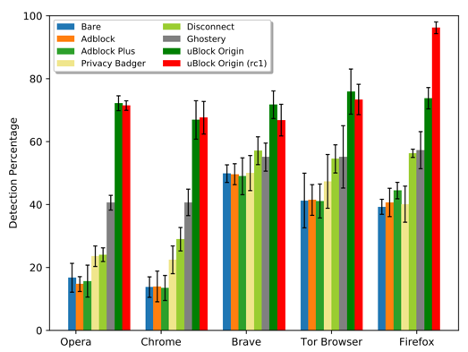
 So what about Vivaldi? Is there something planned for the existing toolbox? M3 will find its way, but this is equally important for what Vivaldi stands for.
So what about Vivaldi? Is there something planned for the existing toolbox? M3 will find its way, but this is equally important for what Vivaldi stands for.moved from General Discussion > Security & Privacy
-
This post is deleted! -
@npro Thanks for the informative articles, I did not know about this. But not really surprising that advertisers will do anything they can to track users, even abusing the DNS system.
I tested in Firefox (+uBlockO) with the site mentioned in the Reg article, and the CNAME host is blocked:
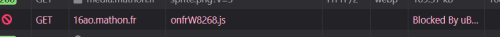
$ dig 16ao.mathon.fr | grep CNAME 16ao.mathon.fr. 187 IN CNAME mathon.eulerian.net. mathon.eulerian.net. 7087 IN CNAME et5.eulerian.net.Do you know how this exactly works in uBlock (Firefox)? Where are the rules or settings to control CNAME blocking, are there special lists?
In principle I definitely agree that requests that use CNAMEs for other domains should not be allowed to set cookies. However, it might cause issues with sites that rely on these cookies for site functions, media playback or similar. The use of CNAME aliases are very common for sites that use a CDN for their content, and it does not have to mean it's for tracking purposes.
$ dig download.vivaldi.com | grep CNAME download.vivaldi.com. 300 IN CNAME downloads.vivaldi.netdna-cdn.com.It could also mean that browsing would be a little slower, as the browser/extension has to check if the host has a CNAME on another domain for each request, and possibly also if that domain is on a tracker-list.
-
@Pathduck said in Brave blocks CNAME tracking, what about Vivaldi?:
The use of CNAME aliases are very common for sites that use a CDN for their content, and it does not have to mean it's for tracking purposes.
Yes, CNAME is not new, it's just that some abuse it which can lead to fatal consequences, I don't remember if this is included in the links above https://docs.microsoft.com/en-us/azure/security/fundamentals/subdomain-takeover
It is a disgusting practice especially when you see it cheered for and being proud about it officially, https://experienceleague.adobe.com/docs/id-service/using/reference/analytics-reference/cname.html?lang=en , this is quite informational how it works, I am not in the position though to follow all details without an extensive study on the matter, which requires a LOT of time, and many many tests with inspecting all 1st-party cookies involved as well, therefore I said that it should be looked and maintained by Vivaldi in the first place.
, this is quite informational how it works, I am not in the position though to follow all details without an extensive study on the matter, which requires a LOT of time, and many many tests with inspecting all 1st-party cookies involved as well, therefore I said that it should be looked and maintained by Vivaldi in the first place.Do you know how this exactly works in uBlock (Firefox)? Where are the rules or settings to control CNAME blocking, are there special lists?
Unfortunately no, I suspect how (what everyone assumes about blocklists) but can't speculate on this, if it's not being taken care though I guess one should study the whole git of uBlock as well, argh...
-
@npro It looks like the code itself is here:
https://github.com/gorhill/uBlock/blob/master/platform/firefox/vapi-webrequest.jsFrom the logger, it looks like it just finds out the CNAME domain, then matches this to existing known trackers from the lists:
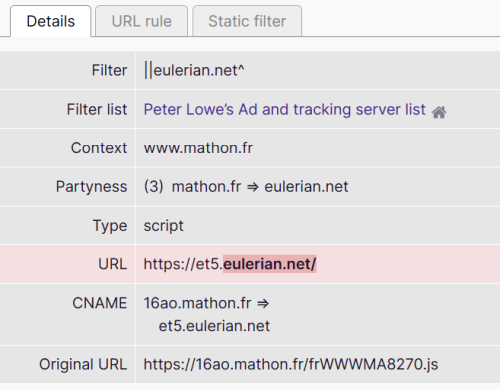
I can't see any setting to toggle this kind of testing on or off if one would want to.
-
@Gwen-Dragon Thanks, wonderful idea!

-
Sorry to necro an old thread, but thought I'd post something that may be of use to future people searching about CNAME-based tracking and Vivaldi.
Pi-Hole correctly checks canonical names, therefore if a site employs CNAME-based tracking, and the "final-destination" tracker server is in Pi-Hole's lists, then Pi-Hole will block it.
So my suggestion would be to put your Vivaldi-running computers behind a Pi-Hole on your local network, at least until the Vivaldi devs get the chance to address this.
On Android, I know that personalDNSFilter (available on F-Droid) also performs CNAME inspection, so you can protect your Vivaldi on Android with that, just like with Pi-Hole. Unfortunately, the app creates a fake VPN to do its filtering, therefore if you use an actual real VPN you won't be able to use it.
DNS66 and Blokada are very popular for Android, and work in the same way, but I haven't used them for a while so don't know if they block CNAME-based tracking.
-
Regarding CNAME from what I read now, 6 months after the initial attempt of someone to provide a rough blocklist, the same method is being used now, treating them like ads, only that this time companies like AdGuard produce them, by filtering offenders through their DNS services. From what I also read they are added to the AdGuard Tracking Protection list, and Easylist probably has integrated them as well. So Vivaldi could already be blocking some of them through Easylist's list.
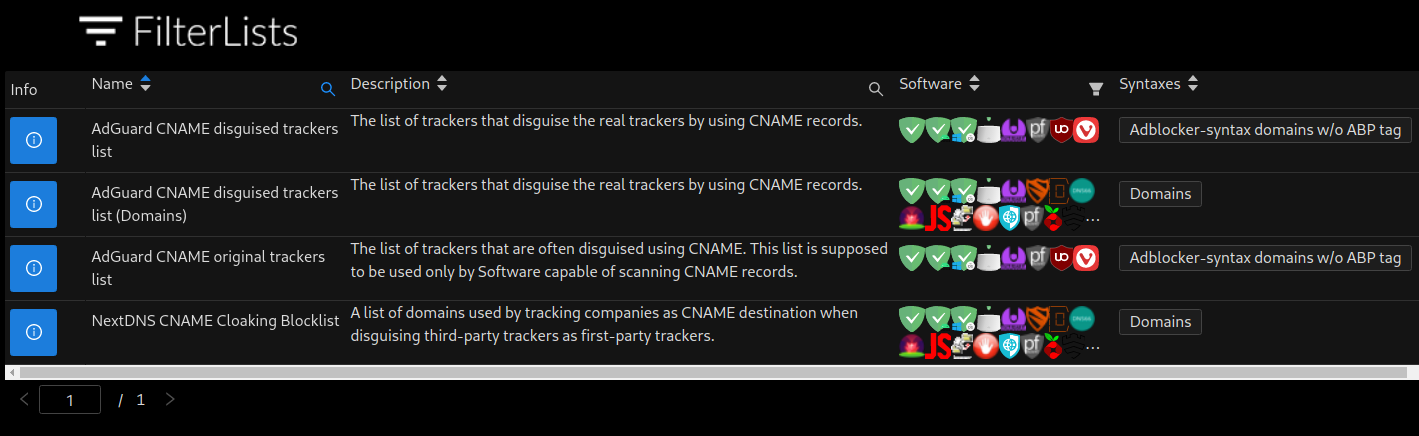
But the point is, what will ruthless clowns come up with in the next 6 months and then in the next 6, which can only be blocked again via filterlists in crappy Chromium. Well the alternative must already be ready and functioning, like Mint did with its Debian Edition.
P.S. Regarding p.2, it's incorporated as far as I know since then, there shouldn't be any rational reason for it to be dropped.
-
@guigirl Does canvas blocker work on a per-tab, per-site, per-session, per-window, or per-api-call basis? (I would prefer per-window)
-
@guigirl That includes...
Third party resources?
First party click throughs?
Third party click throughs?
Frames?
Changes via address bar? -
@guigirl said in Brave blocks CNAME tracking, what about Vivaldi?:
failed to include uMatrix in their tests
uMatrix is unsupported, it's no longer getting updated. So that's no surprise. But uBlock Origin is from the same programmer, and (on advanced mode) has most of the same features as uMatrix.
-
@guigirl Thank for your recommendation.
Users: Prove your Canvas Fingerprint here:
-
@barbudo2005 Umm, the ideal canvas spoofer, in my opinion, would be impossible to detect. That test is just for canvas randomizers I guess. So far I have not found a canvas fingerprint spoofer that is undetectable, perhaps because users like to know IMMEDIATELY that canvas spoofing is enabled.
@guigirl No Spanish Inquisition?

I will test if I have time. -

Mods !!!

-
I think with Trace I have reasonably good protection, aside from Vivaldi's ad / trackerblockers. Everything else that websites want to put on my PC, cookies, caches, serviceworkers ... is blocked by Site Bleacher extension.
