Manifest V3, webRequest, and ad blockers
-
I haven't followed this thread at all, but as far as I remember from trying Adguard MV3 in the past its "element picker" does not work as a firewall the way uBlock Origin works, but still downloads all the content in the background and just hides it for you "afterwards". That's hardly a valid "1:1 alternative", it's basically fake (or at least it was. But I can hardly imagine this has improved, as that's what MV3 is supposed to do, restrict extensions' access to "lower levels".)
I don't even know the state of it but from the little I read it doesn't look that good, few months before MV3. https://adguard.com/en/blog/review-issues-in-chrome-web-store.html
-
Said:
That's hardly a valid "1:1 alternative", it's basically fake..
It is NO fake, just different layout and presentation.
uBO MV2:

You have the option to select
Network filters:||www.biobiochile.cl/assets/escritorio/bbcl-2020/img/bbcl-logo.png$imageor
Cosmetic Filter:www.biobiochile.cl##.py-2.container > [href="https://www.biobiochile.cl"] > .dark-mode-hide.bbcl-logoAdguard MV3:

Cosmetic Filter:biobiochile.cl###header > nav.navbar-bottom:nth-child(3) > div.menu-container:first-child > div.container.py-2:first-child > a:first-child > img.bbcl-logoBut if you select "Block by reference link" you obtain
Network filters:
/assets/escritorio/bbcl-2020/img/bbcl-logo.png$domain=biobiochile.cl
-
@barbudo2005 ok, I will check the status of it again at some point, along with its ability to do dynamic filtering or not.
-
Said:
...its ability to do dynamic filtering or not.
1.- HISTORY OF RULES IN UBO
You can import your "dynamic filtering" from uBO to Adguard:
1.1.-
This:

is this code:
* linkwithin.com * blockYou type block in "My Rules":

And copy the list to Notepad++, and within 5 minutes of few "Find and Replace" you can convert 1000 rules to Adguard:
To this generic code:
||linkwithin.com1.2.-
This:

is:
www.elbuhoentrelibros.com linkwithin.com * noopIn the same way as above you can convert this type of rule to the generic filter code scheme.
2.- NEW SITES AFTER JULY 1
Open the Log and select Third party:


Click Block and you obtain this window:

2.1.-
If you want this:
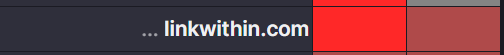
Select this options:

2.2.-
If you want this:

Select this options:

And you obtain:
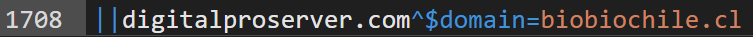
And in the "User rules" you add @@ at the beginning:
@@||digitalproserver.com^$domain=biobiochile.cl -
Remember that if you have been using uBO for 5 or more years your “My Rules” list behaves like this curve:

Where the horizontal indicates the number of years and the vertical indicates the number of rules.
-
@barbudo2005 This does not apply to me as I basically block all 3rd-party scripts and frames and/or 1st-party so I work basically by adding exceptions with every site I visit. I saw your previous post so from the looks of it it seems that I would need to work with the log window involving numerous clicks, in that regard uBO has better visibility and usability, so we 'll see.
-
@npro Also let's not forget that neither Adguard/uBO for Chromium-based browsers, nor Vivaldi's built-in adblocker support CNAME uncloaking, you need to use uBO on FIrefox (& forks) or Brave's built-in adblocker for that.
-
@npro said in Manifest V3, webRequest, and ad blockers:
CNAME uncloaking
Andi said:
NextDNS introduced CNAME uncloaking support in November 2019 as the first cross-platform solution to block disguised third-party trackers[^1]. This feature protects against CNAME cloaking, where tracking companies hide third-party trackers as first-party trackers using DNS records[^2].
The implementation works by applying blocklists to intermediate CNAME records during DNS resolution, rather than just checking the queried domain name[^3]. This approach is more effective than browser-based solutions since it operates at the DNS level and can detect trackers regardless of how they are disguised[^2].
Some issues emerged in 2022 when Chrome users reported that secure DNS (DoH) settings became disabled and showed as "managed by organization"[^4]. This bug affected both Chrome and Brave browsers but was fixed in Brave version 1.40.109[^4].
NextDNS maintains its own CNAME cloaking blocklist that focuses on tracking companies' destination domains rather than individual hostnames[^5]. According to NextDNS, this approach requires less frequent updates compared to lists that track all new hostnames pointing to those CNAMEs[^5].
[^1]: NextDNS added CNAME Uncloaking support, becomes the first cross-platform solution to the problem
[^2]: CNAME Cloaking, the dangerous disguise of third-party trackers
[^3]: Web trackers using CNAME Cloaking to bypass browsers' ad blockers
Also Portmaster can be an solution, browsers, even Brave, FF and even TOR can't avoid it 100%, it must be done on system level.
Ad blockers such as AdBlock, Adblock Plus, and uBlock Origin are blindside by the CNAME Cloaking tactic because browser extensions are not allowed access to the DNS layer of web request, so they can’t see the CNAMEs.
-
@Catweazle I just tried nextDNS, it doesn't work with my global DoT system configuration -maybe it needs an account-, so
 . No idea what portmaster is, I'll read about that at some point, so at the moment I'll just stay with my currently working configuration.
. No idea what portmaster is, I'll read about that at some point, so at the moment I'll just stay with my currently working configuration. -
@npro, Portmaster is an network manager and firewall, it permits to control and block, if needed, any in and outgoing traffic from any installed app. Customizable Filterlists include dynamic filterings.
Very easy and intuitive UI, very good default settings, so normally no need to change much, it's intalling and forget.
Optional an SPN service (paid), something like an VPN on steroids, inspired by the TOR network.
It's OpenSource, very recommended.



 *
*