Want to Ignore invalid certificate of a device
-
Please tell me how I can provide you with a "short log export". I already did a mostly short log export with all relevant information trivially visible (but everything else being stripped), but it is too long to post here. How can I provide you a log file for further analysis.
-
@patrickweiden said in Want to Ignore invalid certificate of a device:
Vivaldi_Snapshot\Application\vivaldi_proxy.exe --profile-directory=Default --debug-packed-apps --silent-debugger-extension-api --process-per-site --enable-quic --quic-version=h3-29 --ignore-certificate-errors
First of all, why are you calling vivaldi_proxy instead of vivaldi.exe directly?
And yes, remove the QUIC flags, do you even know why you have those? QUIC has been enabled by default for a very long time now, no need to enable with flags.
And what's that
--process-per-siteabout? You really shouldn't run experimental cmd switches without being 100% sure what good they do. Documentation for the switch says: "You probably want the other one."
https://peter.sh/experiments/chromium-command-line-switches/#process-per-siteIt certainly doesn't hurt to remove them for testing and that's one of the first things I would've done. Everything that differs from defaults are potential error causes.
Also:
- Have you tried Vivaldi in a clean profile to exclude any other flags you've messed with or installed extensions causing problems?
- Google the make and model of your device and the error message to see if anyone else has had the same problem?
- Run the
sslscanandopenssltests to get some details on what exactly that device is using/supporting. - Get a net-export log and analyse the requests for details about the protocol used.
- This looks like it's a Standalone install? Try a Stable install instead of Snapshot, it also works as a clean profile test of course.
-
@patrickweiden said in Want to Ignore invalid certificate of a device:
Please tell me how I can provide you with a "short log export". I al
Not sure what you mean by "short log"? Have you captured a log from
vivaldi://net-export? You can analyse it yourself in the netlog viewer, you seem like the technical sort, I'm sure you can understand how it works
Like I said earlier, to get only data from the device connection you should close all other tabs creating network traffic and focus on recreating just the issue, no other traffic causing an irrelevant mess of logging. Ideally run the capture in a clean profile.
"SOCKET" is the kind of connections you'd be interested in looking at.
The net export log will naturally contain some internal info like IP etc, the "strip private information" option does not remove this. But if you zip and upload it somewhere I can take a look (or DoctorG). Make sure to specify what to look for and relevant timestamps/addresses.
-
@Pathduck said in Want to Ignore invalid certificate of a device:
@patrickweiden said in Want to Ignore invalid certificate of a device:
Vivaldi_Snapshot\Application\vivaldi_proxy.exe --profile-directory=Default --debug-packed-apps --silent-debugger-extension-api --process-per-site --enable-quic --quic-version=h3-29 --ignore-certificate-errors
First of all, why are you calling vivaldi_proxy instead of vivaldi.exe directly?
No specific reason except I found it somewhere in the forum, I think.
And yes, remove the QUIC flags, do you even know why you have those? QUIC has been enabled by default for a very long time now, no need to enable with flags.
And what's that
--process-per-siteabout? You really shouldn't run experimental cmd switches without being 100% sure what good they do. Documentation for the switch says: "You probably want the other one."
https://peter.sh/experiments/chromium-command-line-switches/#process-per-siteIt certainly doesn't hurt to remove them for testing and that's one of the first things I would've done. Everything that differs from defaults are potential error causes.
I removed the flags for testing, created a new profile, tested, it did NOT help.
I then closed the "main window" just to be left with the new profile to run net export.
(See below.)Also:
- Have you tried Vivaldi in a clean profile to exclude any other flags you've messed with or installed extensions causing problems?
Yes, as written above. No help.
- This looks like it's a Standalone install? Try a Stable install instead of Snapshot, it also works as a clean profile test of course.
It is a standalone install. The stable version has the same problems.
- Get a net-export log and analyse the requests for details about the protocol used.
[...]
"SOCKET" is the kind of connections you'd be interested in looking at.
The net export log will naturally contain some internal info like IP etc, the "strip private information" option does not remove this. But if you zip and upload it somewhere I can take a look (or DoctorG). Make sure to specify what to look for and relevant timestamps/addresses.

I pasted it to pastebin, password-protected and to expiry in a week.
I will send you the password via message./edit: The relevant information is that XXX.XXX.XXX.ZZZ is the target, XXX.XXX.XXX.YYY is the source, and XXX.XXX.XXX.AAA is the gateway of the (same) subnet. I think there is one irrelevant IP adress inside which is pseudonymized to XXX.XXX.XXX.FFF or so. This should be all needed for the analysis why the connection to the target address port 443 is not being established (I hope). If not, please ask via chat. Thank you very much!
- Google the make and model of your device and the error message to see if anyone else has had the same problem?
- Run the
sslscanandopenssltests to get some details on what exactly that device is using/supporting.
Those I may be doing later or tomorrow.
-
@patrickweiden May is ask more:
-
For the printer, typing
thisisunsafewhen SSL error page appeared had not worked for you? -
When Vivaldi did not connect to your printer which error message was shown?
I mean a string f.ex. like NET::ERR_CERT_COMMON_NAME_INVALID?
What is shown if you click on the error message string?
It is not easy to debug SSL/TLS and cipher errors of a device on Windows.
Programs like sslscan can help to get all available SSL/TLS protocol and ciphers of the device. -
-
@DoctorG: When I try to connect to the printer, the following is shown by Vivaldi:

What do you mean exactly with your first point? Where shall I type
thisisunsafe?https:\\PRINTER_IP\thisisunsafe? -
@patrickweiden When the error page appears do not leave page, do not focus URL field, just type blindly
thisisunsafe.Which SSL/TLS versions and ciphers did a scan with sslscan showed for your printer?
Please post text here with </> button, for privacy change printer name and IP to ***. -
@DoctorG said in Want to Ignore invalid certificate of a device:
@patrickweiden When the error page appears do not leave page, do not focus URL field, just type blindly
thisisunsafe.Thank you for the description. What is supposed to happen? I am asking because for me nothing happens.

Which SSL/TLS versions and ciphers did a scan with sslscan showed for your printer?
Please post text here with </> button, for privacy change printer name and IP to ***.I will do this, but I will not have time before today evening. As soon as I have done this, I will post it here as mentioned.
-
@patrickweiden said in Want to Ignore invalid certificate of a device:
What is supposed to happen? I am asking because for me nothing happens.
After you typed thisisunsafe the error page should disappear and the printer page should appear with a red
 ️ in adressbar instead a lock.
️ in adressbar instead a lock.I will do this, but I will not have time before today evening
All good, i will answer when you(!) have spare time.
-
@DoctorG said in Want to Ignore invalid certificate of a device:
@patrickweiden said in Want to Ignore invalid certificate of a device:
What is supposed to happen? I am asking because for me nothing happens.
After you typed thisisunsafe the error page should disappear and the printer page should appear with a red
 ️ in adressbar instead a lock.
️ in adressbar instead a lock.I am sorry to tell you this, but with me nothing happens after the screenshot above with the error message "This site can’t provide a secure connection" appears. No loading of page etc.
I will do this, but I will not have time before today evening
All good, i will answer when you(!) have spare time.
In some sense I am sorry but I have several meetings over the day and cannot necessarily provide the required information on time.
-
@patrickweiden said in Want to Ignore invalid certificate of a device:
I am sorry to tell you this, but with me nothing happens after the screenshot above with the error message "This site can’t provide a secure connection" appears. No loading of page etc.
Then the thisisunsafe-typing does not work for all SSL issues. may be a Chromium core restriction in Vivaldi.
-
@patrickweiden Hi, sorry for the late reply. I did have a look at the log, unfortunately nothing more enlightening.
The relevant socket connection(s) show:
t=3205 [st=23] SSL_HANDSHAKE_ERROR --> error_lib = 16 --> error_reason = 1040 --> file = "..\\..\\chromium\\third_party\\boringssl\\src\\ssl\\tls_record.cc" --> line = 594 --> net_error = -113 (ERR_SSL_VERSION_OR_CIPHER_MISMATCH) --> ssl_error = 1But I was hoping it would show at least TLS version or what cipher used. I know it does for a working socket connection:
t=1319 [st= 8] SOCKET_BYTES_SENT --> byte_count = 517 t=1457 [st=146] SOCKET_BYTES_RECEIVED --> byte_count = 1360 t=1457 [st=146] SSL_HANDSHAKE_MESSAGE_RECEIVED --> bytes = 02 00 00 55 03 03 4E 30 DE 17 29 56 CC 29 66 78 . U..N0..)V.)fx DA FC 02 78 27 B7 1C 0B 3E 2D 37 4B 63 C0 1A 0B ...x'...>-7Kc... 4A BD 55 A3 EB 9B 20 F1 A4 78 8C 02 4B 52 EE 1F J.U... ..x..KR.. FB 5B A2 61 DB 10 31 92 BD 7B 14 52 28 84 E7 3C .[.a..1..{.R(..< 7C EC 34 4A 34 E5 8E C0 2F 00 00 0D FF 01 00 01 |.4J4.../ ... . 00 00 0B 00 04 03 00 01 02 . .. .. --> type = 2 t=1490 [st=179] -SSL_CONNECT --> cipher_suite = 49199 --> encrypted_client_hello = false --> is_resumed = false --> key_exchange_group = 23 --> next_proto = "unknown" --> peer_signature_algorithm = 1537 --> version = "TLS 1.2"In this case cipher_suite is 49199:
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256In your case a SSL handshake is sent but hardly anything is received:
t=3197 [st=15] SOCKET_BYTES_SENT --> byte_count = 517 t=3205 [st=23] SOCKET_BYTES_RECEIVED --> byte_count = 7 t=3205 [st=23] SSL_ALERT_RECEIVED --> bytes = 02 28So yeah, still no idea why Chromium browsers fail connecting to your device.
Does it listen on plain http and does it work?
@DoctorG said earlier:
"TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 works only if TLS 1.3 is active, tested with Firefox 103 and Chromium 104!"So maybe it tries to use this cipher with an older TLS version (1.0/1.1/1.2?). And maybe Firefox is more forgiving and you've also explicitly set a security exception for this site.
This is why it would be interesting to see
sslscanoutput and alsoopensslconnect output, maybe even trying to do acurlto the device HTTPS interface:
curl -I <device>:<port> -
@Pathduck: You wrote:
You can get the OpenSSL binary from here if you don't have it: https://wiki.openssl.org/index.php/Binaries
This is what my browser currently finds there:
Should we tell the OpenSSL guys about it?

/edit: This morning it works again.

Nevertheless, I managed to organize myself some OpenSSL 3.0.5 binaries to run it...
I ran the
openssl s_client -connect PRINTER-IP:443command and received the following output:
And the
sslscan PRINTER-IP:443led to the following results: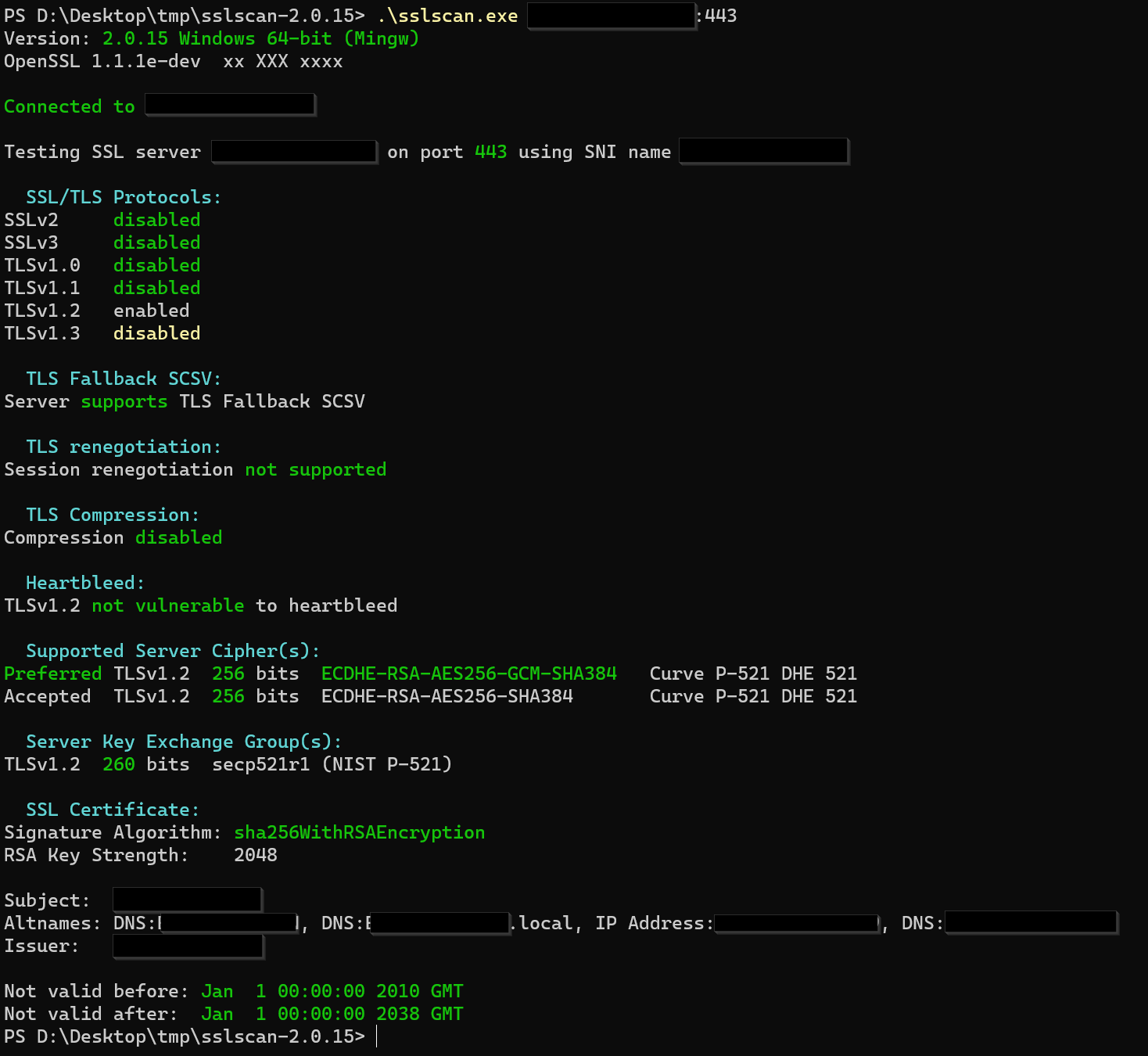
I removed all "irrelevant information" as (DNS) names, IP addresses etc. The certificate is a self-signed certificate from issuer "PRINTERNAME" to subject "PRINTERNAME". If you need further information, please ask for it. Thank you!
/edit:
Does it listen on plain http and does it work?
It has a built-in option to redirect HTTP to HTTPS, which is enabled. I deactivated this redirection and Vivaldi was able to connect to the insecure HTTP variant. The HTTPS variant is still not accessible via Vivaldi (if you explicitly try to reach it via
https://PRINTER-IP).
But at least for the "admin interface" the HTTPS variant should work as you need to enter the admin password (and I do not want to enter it on HTTP variant of the website), so using the HTTP variant is not a real solution here.../edit2:
@DoctorG said earlier:
"TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 works only if TLS 1.3 is active, tested with Firefox 103 and Chromium 104!"
According to this site the mentioned cipher suite also works with TLS 1.2:

So, should not be any issue here as it has been presented by the printer...
-
@patrickweiden Hmm,
seems all ok.
 I do not understand why the printer has only one cipher for TLS 1.2. Weird!
I do not understand why the printer has only one cipher for TLS 1.2. Weird!Connect by IP gives always an error as certificates are only valid for a domain.
-
Heureka!
https://bugs.chromium.org/p/chromium/issues/detail?id=478225
https://bugs.chromium.org/p/chromium/issues/list?q=secp521r1&can=1The secp521r1 is algorithm which is not regarded as secure anymore (weakness was infiltrated by NSA) and removed by Chromium devs.
Can not be enabled by command line or any other internal setting.
-
@Pathduck said in Want to Ignore invalid certificate of a device:
@DoctorG said earlier:
"TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 works only if TLS 1.3 is active, tested with Firefox 103 and Chromium 104!"I could be wrong with test on my crazy web server. Sorry.
-
@patrickweiden can the SSL/TLS on printer administrated to use other ciphers?
Use of only one with the weak cipher suit is really unusual. -
@DoctorG said in Want to Ignore invalid certificate of a device:
@patrickweiden can the SSL/TLS on printer administrated to use other ciphers?
@DoctorG: I was able to change the key size from 256 bits to 192 bits, now "Server Key Exchange Group" section of
sslscansays:TLSv1.2 192 bits secp384r1 (NIST P-384)So, the questionable
secp521r1is no longer in use.Now I can open the website, the only remaining thing is the self-signed certificate. But this I can handle.

Thank you very much for your support!
-
@patrickweiden said in Want to Ignore invalid certificate of a device:
the only remaining thing is the self-signed certificate
Download the public key of the cert and import in your Windows Certificate Store in tree "Trusted Root Certificates"; that helped in the past with self-signed certificates.
-
@DoctorG said in Want to Ignore invalid certificate of a device:
@patrickweiden said in Want to Ignore invalid certificate of a device:
the only remaining thing is the self-signed certificate
Download the public key of the cert and import in your Windows Certificate Store in tree "Trusted Root Certificates"; that helped in the past with self-signed certificates.
Yes, this did help. Entering the subject name of the certificate as
https://CERT-SUBJECTdid yield a valid certificate and now I am even able to store the credentials (which Vivaldi did not offer before due to "invalid certificate").
