[BUG] Vivaldi shows wrong certificate info
-
This is a screenshot from today (2024-08-15):
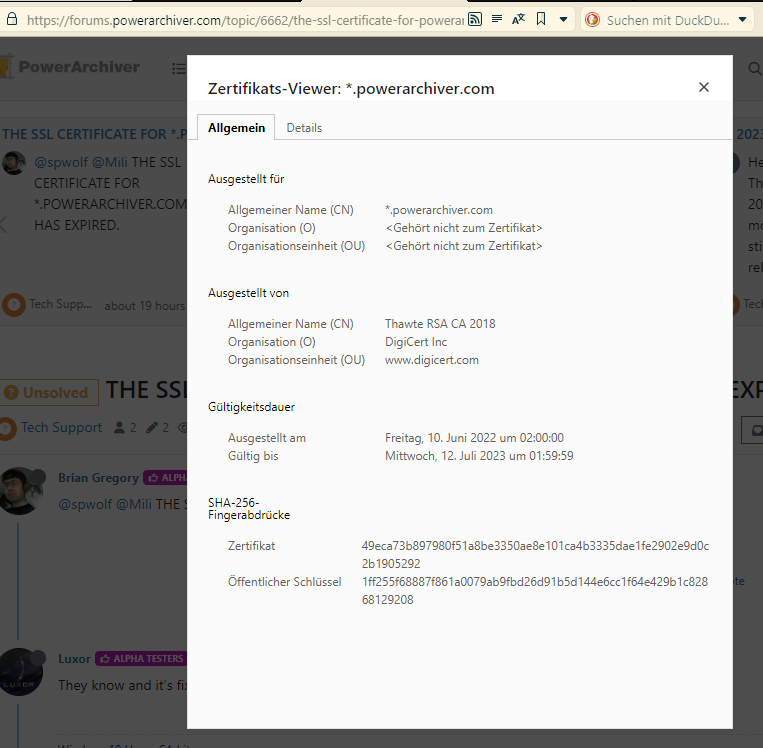
Vivaldi tells me, that the connection to the site https://forums.powerarchiver.com is secure, but the certificate properties show, that the certificate is expired.
Note, that https://www.powerarchiver.com provides also a certificate for *.powerarchiver.com, which is indeed valid. Using https://de.ssl-tools.net/webservers/forums.powerarchiver.com#4799b49d3efba3e06c640b07986e2de0b33eef3c, I get the same certificate for the site as for www.powerarchiver.com, so it seems, Vivaldi mixes something up. -
Nope, shows fine here...
Tried clearing cache or reloading with Ctrl+F5?
-
@BigMike All ncie on my 6.8 Vivaldi.

-
@BigMike All ok with the server!
Checked at: -
@BigMike Perhaps your Vivaldi cached a old certificate.
Openvivaldi://net-internals/#hsts, go to Delete domain security policies , add in field Domain the textforums.powerarchiver.comand hit Delete.
Openvivaldi://net-internals/#hsts, go to Delete domain security policies , add in field Domain the textpowerarchiver.comand hit Delete.
Restart Vivaldi.Or something on your system gives you a faked certificate with the SSL connection!
-
@BigMike The certificate public key for both certificates are the same, which would mean that if you had a valid SSL session with the server from before the website admins fixed the certificate then it would not be renegotiated unless the server admins also had flushed the sessions when fixing the certificate (which they evidently didn't; and they should also have changed the key when requesting the new certificate).
That current session means that when viewing the certificate details you will see the (expired) certificate that was used at that time, not the present (unexpired) certificate.
The reason you had a "valid" session was very likely because you had approved the expired certificate previously (which you should not have done; "expired" warnings mean "run away, run away", not "Oh, I am sure it is really OK, nobody would steal an expired certificate").
-
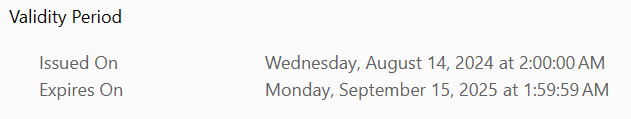
@yngve, I see a valid date until 2025, but also this

-
@Catweazle That is a misconfiguration, and something that can easily be fixed server side. Strictly speaking the root can be sent, it is just not done normally.
This particular intermediate (Thawte) is actually a cross-sign for one of the Verisign Roots that Digicert took over when Verisign was untrusted by all browser some years ago (they issued tens of thousands of test certs from production CAs for domains they did not own or control). It looks like the brand is still kept alive.
Clients are generally able to complete chains in these cases, either because they have many of the intermediates (in addition to the trusted roots) in their certificate repository, or because the intermediates can be downloaded (and have to trace to a trusted root in order to be used).
-
Thank you all for looking into this and your replies.
Today, the new certificate is displayed in the cert info dialog.The reason you had a "valid" session was very likely because you had approved the expired certificate previously (which you should not have done; "expired" warnings mean "run away, run away", not "Oh, I am sure it is really OK, nobody would steal an expired certificate").
- Well, first, I didn't know, that the certificate exceptions are permanent, and not for the current session only. Thanks for pointing this out.
- How can I clear my exceptions? I can't find any settings for this behavior; I can't tell you if I acknowledged this once, as the presented certificate expired in 2023...
- What's the correct way to visit a web site and don't add the exception permanently?
- Second: Comparing to https://expired.badssl.com Vivaldi warns me with an exclamation mark after adding the exception, while it didn't with https://forums.powerarchiver.com
Edit:
- I just noticed, on expired.badssl.com that I can clear the exception on the site, when I click on the exclamation mark in the address bar.
So: For forums.powerarchiver.com, there was no exclamation mark, but a padlock and the connection was displayed as secure. - I'd like to request to have a list with all my exceptions in the settings.
- And I'd like to request to have the choice to allow the bad certificate just for the current session and all time. ["run away, run away" works only in theory]
-
@BigMike The best way to make it a temporary exception is by using a Guest Profile or a Private Window, as those are by design temporary.
As long as the excepted certificate is in use by the site you can remove the exception. (the exception depends on the binary value of the certificate).
Anything more advanced is something that really need to be implemented by the Chromium devs. My guess, though, is that they don't think it is worth the effort, and may also think that for public production sites (as opposed to private/company internal sites) the user should complain to the site, and wait for the fix.
For that matter, they probably think, as I do, that public sites should never have an expired certificate (and if they accidentally do, they should fix it in the middle of the night if necessary); in fact there are now scripts for automatic renewal and installation of certificates, called ACME (I don't think there is a coyote involved with this one, so it probably won't blow up the server), which are especially used for the Let's Encrypt certificates that are only valid for a few months.
I am wondering if your problem site was using several server mirrors, and one wasn't properly configured with the most recent certificate (happens now and then, especially when not using ACME), and that might have caused hiccups in the padlock algorithm. Maybe they also re-enabled an old mirror, with a bad configuration, which may be possible, considering that the bad certificate was a year and a month out of date, and the newer one is valid for 13 months (and was installed 4 days ago, after somebody complained), which suggest that they had the same problem last year (13 months ago).
-
@yngve Thank you for your detailed information.
I'll go with a private session next time

Honestly, I'm not a fan of information on certificates and encryption settings in modern browsers.

But thank you again. All is fine for me not.
