Use secure DNS (DoH) - Disabling without effect
-
I disabled the setting "Use Secure DNS" in vivaldi://settings/security. Unfortunately Vivaldi still uses DoH.
Tested with a fresh Snapshot 6.2.3060.3 without any changes (No extensions, no VPN, no ...) with Ubuntu 20.04.LTS. I use Pi-Hole with the unfiltered and uncensored DNS Server Quad9 and digitalcourage.
"Use Secure DNS" is enabled by Vivaldi default.
Netlog Viewer shows: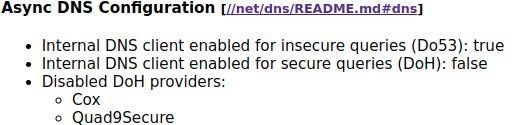
I don't need "Use Secure DNS" and this setting generates double DNS requests.
In my case since ~20.05.2023 around 250k requests. What a waste of resources and money.The only way, I found to stop DoH is: Disable "Async DNS resolver" via vivaldi://flags.
Is this behaviour desired or a bug?
-
@mottenmouse said in Use secure DNS (DoH) - Disabling without effect:
Unfortunately Vivaldi still uses DoH.
How can you tell?
Netlog Viewer shows
The image shows the client is enabled for "insecure" queries (Do53) which is regular DNS over UDP port 53.
You will see this in the Netlog event viewer as UDP connects to port 53 of your system DNS server.
The only way, I found to stop DoH is: Disable "Async DNS resolver" via vivaldi://flags.
This will disable the browser's DNS client and fall back to using your OS' DNS resolver. Which of course is fine. The reason browsers have their own client is generally because of latency (asking the OS first) and to be able to do stuff like DoH in the first place.
-
OK, wrong choice of words.
Regardless of the "Use Secure DNS" setting, an HTPPS request is initiated and I see in the Pi-Hole log file:
and in the Wireshark log file:

The "HTTPS" request will be answered always with "unknown".
Question: Why do I get the HTTPS request when DoH is deactivated, which in my eyes is useless and data rubbish? This is what "Unfortunately, Vivaldi is still using DoH." refers to. Actually, I should add "???" at the end of the heading ;).
I don't know if DoH is even possible with my overall configuration (router, Pi-hole, OS, browser). I don't think so without really knowing.
Arguments about latency, security, sense, etc is a whole other topic and really has nothing to do with the post.
-
@mottenmouse There's nothing in those pictures that indicate a DoH request. In Wireshark, it clearly says "DNS" which is not DoH - DoH has its own protocol type in Wireshark.

The "HTTPS" you're seeing is a standard DNS request for a "HTTPS" DNS record.
https://en.wikipedia.org/wiki/List_of_DNS_record_typesBefore using all that strong language and getting all bombastic, it's important to understand the topic you're discussing.
-
@mottenmouse I suspect that "HTTPS" in this case refers to a query for the "Please provide the address details for the HTTPS service associated with forum.vivaldi.net"
DNS have two different modes: "Addresses" (A) and "Services" (the protocols, such as HTTPS, normally associated with 443)
-
-
@mottenmouse Hey, don't worry about it - happy it helped clear things up

I do have to say, I have noticed a lot of people using Pi-hole but lacking basic networking knowledge, which is kind of worrying - because when stuff inevitably breaks they will have a hard time troubleshooting it. Nobody needs to be a networking expert - I'm certainly not - but Pi-hole is a complicated piece of software (even if relatively easy to install and setup).
Some things:
I don't know if DoH is even possible with my overall configuration (router, Pi-hole, OS, browser). I don't think so without really knowing.
With DoH enabled in the browser it will use HTTPS (port 443) for DNS queries, and this will pass right through just like a regular web request.
I don't use DoH myself, and I don't like it. Mostly because it complicates any local DNS troubleshooting, hiding everything as encrypted packets from the browser. When I have DNS resolution issues, I like to examine what's going on between my system and router without needing to decrypt browser traffic to do it.
Lastly, I'd recommend you add the Src/Dst Port fields to the output of Wireshark, it help understand what goes on - you would've seen that the port was 53 and that DoH was not in use

-
@mottenmouse said in Use secure DNS (DoH) - Disabling without effect:
Somehow I regret writing with my rudimentary knowledge.
No problem.
Debugging network with Wireshark was never easy. Som knowledge is needed on packets, protocol types, SSL, and so on.
