Canvas Defender, uBlock Origin: General page protection.
-
I've just become aware of this https://chrome.google.com/webstore/detail/canvas-defender/obdbgnebcljmgkoljcdddaopadkifnpm?hl=en-GB Canvas Defender. Given i've long been hoping for V to implement native blocking of Canvas Fingerprinting, i thought i'd look into this. I've tested it in Chromium & V-SS. It seems to work [i set the timer to 6-hrs, but also i tested with manual noise changes]. Am i missing something? Does anyone have any opinions on this extension's:
- Effectiveness
- Safety / Integrity / Bona Fides
-
This looks interesting. It seems to work properly; successive tests with 1 minute change interval show unique but constantly-changing canvas IDs, so they might get worthless.
I can't say much about the safety of the extension; a first look didn't reveal any obvious or obviously-hidden data exfiltration code (which seems of most concern with unknown extensions).
I can recomment the change to the extension code which is described in one of the reviews (disable notifications), as it does spam notifications imho...
I'll continue trying out this one, but I'll still continue browsing with JS disabled

-
Definitely seems interesting, but like this company mentions on one of their blog posts, unless you combine it with a bunch of other anti-fingerprinting measures it won't be a total solution.
Perhaps useful in the meantime, but I await the day that Vivaldi builds in more measures against fingerprinting.
I also wonder if there would be a way to identify the presence of whatever script they are using to modify the canvas. If you can detect that, then it renders the whole extension useless.
The best solution is probably to (as @Morg42 says) just disable as many scripts as possible.
-
@morg42 said in Canvas Defender:
browsing with JS disabled
Inspired by this idea, i disabled JS in Settings. Some of my regular sites still work, but others are broken, including...
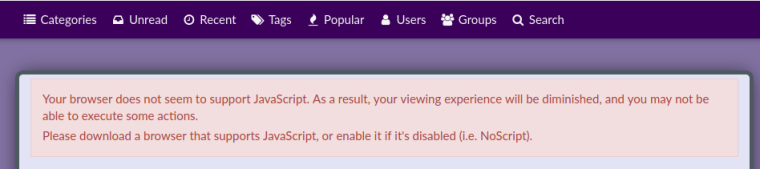
I could not even make this Reply, til i re-enabled it for this site. Sigh.
"a first look didn't reveal any obvious or obviously-hidden data exfiltration code" --> yes, this is exactly what i was wondering about. It would be horrible if using this extension resulted directly in data-theft, but i am not skilled enough to know how to test for it.
-
Steffie, disabling JS completely might be safest, but is prone to leave an internet quite dull...:)
I'm using Scriptblock (https://chrome.google.com/webstore/detail/scriptblock/hcdjknjpbnhdoabbngpmfekaecnpajba), which allows to temporary and selectively enable JS while generally disabling it. You can whitelist sites you trust or "need to use" with JS. A predecessor of this extension provided good services also in early Opera.
In addition, my settings in uBlock Origin disable inline scripts, 3rd party scripts and 3rd party resources generally and will only be enabled for selected sites (and even then mostly only temporary, though UO supports storing site preferences).
I would guess that a bit over 1/2 of all sites work if 3rd party resources (static images, static CSS or similar) are enabled, but with JS completely blocked. Another 20-25% work if JS only for that site are enabled. The rest (about a quarter) need external scripts. I found that on sites where I don't feel good enabling JS, I mostly get to decide I don't need this specific site. Not too shabby a feeling

-
@morg42 OMZ, this is really good info - thank you. The trouble with helping me, as you have done, is that i'm likely to just come back with more questions. Sorry, but...
- After my previous post, i was a few hours away from the V forum, doing some tests as follows [after these numbered points], so i didn't see your post til now. I've now [c/o your heads-up] looked at Scriptblock, & from one comment there also ScriptSafe. i feel inclined to install one or other, possibly the latter, but i'd like to ask... do these extensions give better overall performance [balance of protection but still with reasonable site efficacy] than what i tested [below], namely disabling JS globally in V then whitelisting sites that are broken?
- Did you specifically rule out ScriptSafe in lieu of Scriptblock?
- "my settings in uBlock Origin disable inline scripts, 3rd party scripts and 3rd party resources generally" ... i've just glanced at my uO settings but didn't notice such things. Would you be kind enough pls to share how you did this?
Here's the clumsy test i was doing. It made me so frustrated, coz i hadn't even finished testing anywhere near all my important regular sites, yet of those i did test most were broken & had to be whitelisted... which begs the question; what's the damn point? Sad face. I mean, if JS exploits are invisible to users, or at least to numpties like me, & if potentially any site might be able to be infected, then any of my whitelisted sites now or in future could begin harvesting my data & i'd never know, meaning that globally blocking JS but then exempting heaps of sites important to me, offers NO better protection to simply leaving JS globally enabled. I am not a tinfoil person, but honestly i find this stuff truly demoralising.
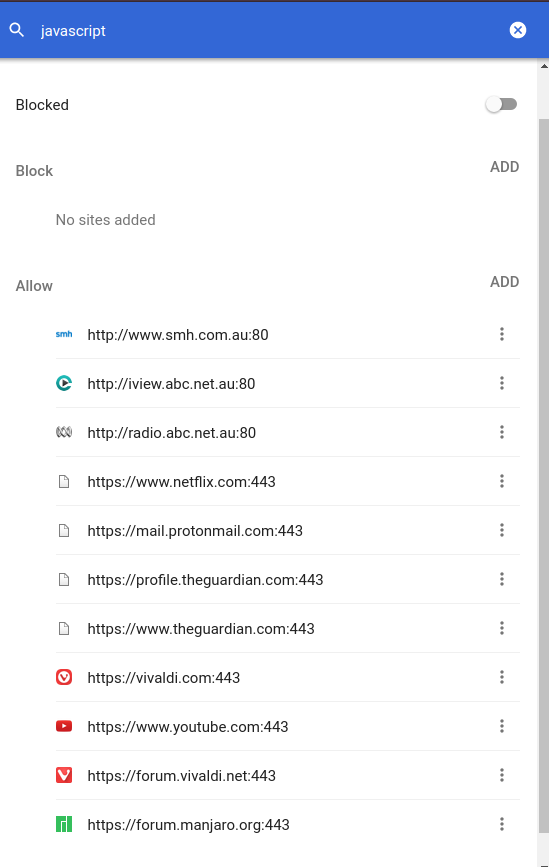
Another sad face, just because.
-
@purgatori Thanks heaps! OK, post-lunch i now have my afternoon project
 Let the [/my] headache commence [soon].
Let the [/my] headache commence [soon].Expect more feeble questions, later...
-
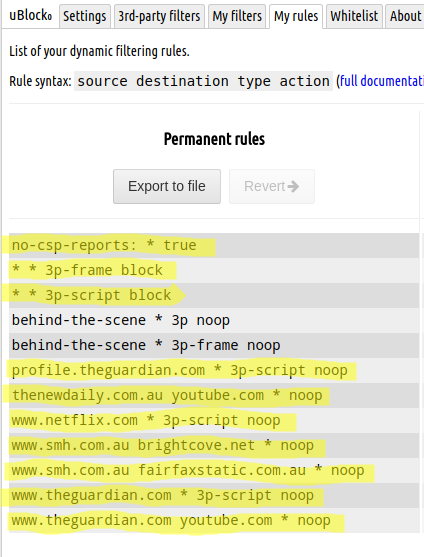
@purgatori It's taken a few more hours of re-re-re-reading https://github.com/gorhill/uBlock/wiki/Dynamic-filtering:-quick-guide then experimenting with lots of my fav sites, but finally i think this is making some workable degree of sense to me. Consequently, i've still not [yet?] installed either of those script-blocking extensions, still do have Canvas Defender installed & enabled [timer still 6 hrs], have re-enabled JS in chromium Settings, & wrt my uO [yellow highlight denotes new changes from today's exercise; also, some of my fav sites didn't break after globally enabling the 3rd-party frame & script blocks, but for the ones that did, the settings below show the solutions (being dim, it took me ages to grasp the functional difference between Green (Allow) & Grey (NoOp))]:
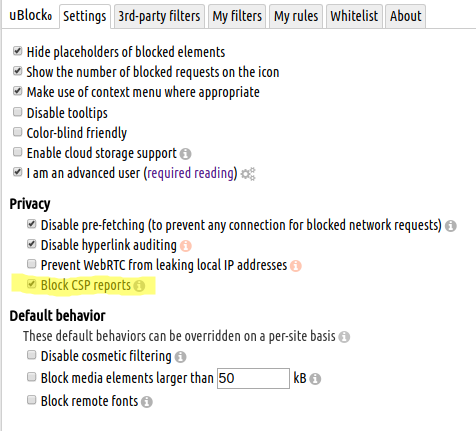
.
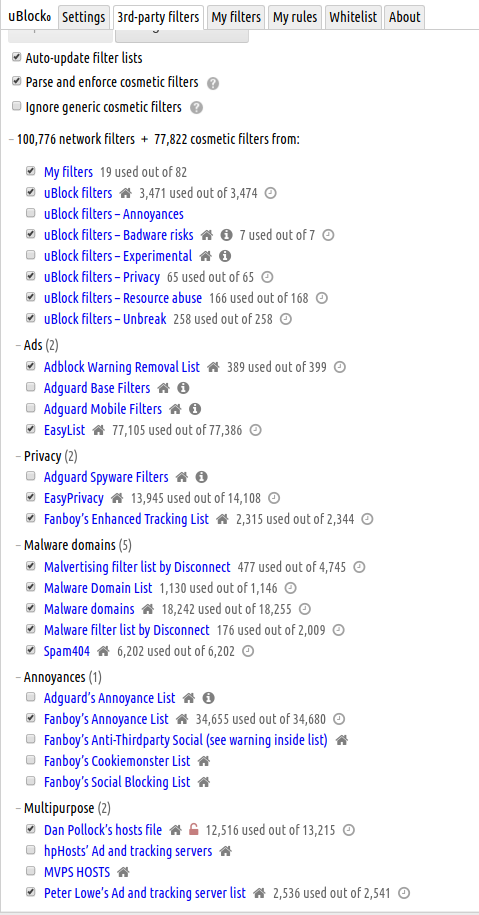
.
.
.
Thank you again! -
My fingerprint only detects my SO, Vivaldo is not even displayed as my browser, but like Chrome, according to this test
https://browserleaks.com/canvas
I use only Genesis Plus adblocker (and Quad9 DNS), nothing else, I don´t have desactivated Java
-
@purgatori You also have to consider that some first party sites might be serving tracking scripts like canvas fingerprinters.
I think that would be unlikely as most tracking / big data analysis is probably going to be outsourced for smaller sites, but some of the bigger ones might well be doing it.
-
@purgatori Yeah, what you said !!

Another few hours of testing, & though lots more of my regular sites work fine w/o needing any finessing of uO, i have had to further enlarge my dynamic filtering rules list for several others. The current status of said list now includes 10 x 3p-script noop entries.
To ask a revised version of a question of many hours ago, what stops me being exploited in future, if any of those 10 sites gets hacked, now that i have had to allow 3rd party scripts there [otherwise, the sites simply don't work]?
My presumed answer is... nothing; if that happens, i'm screwed.
?
-
Sorry for deleting this elaborate piece of work - but seeing that I have additional sources to make you afraid of JS and it really didn't belong in this thread, I rewrote the whole thing and posted it here:
-
@morg42 That is a masterful exposition - hearty thanks to you.
I have now modified the thread title, so i think it's ok to continue herein.
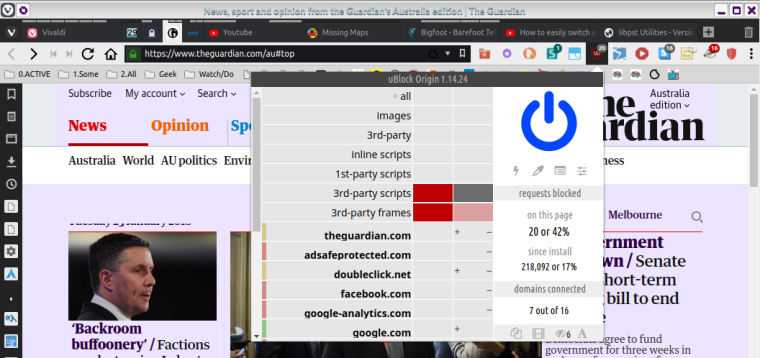
As of the end of my experimenting yesterday, this was/is my current uO status for Guardian [to keep using this example]:
&
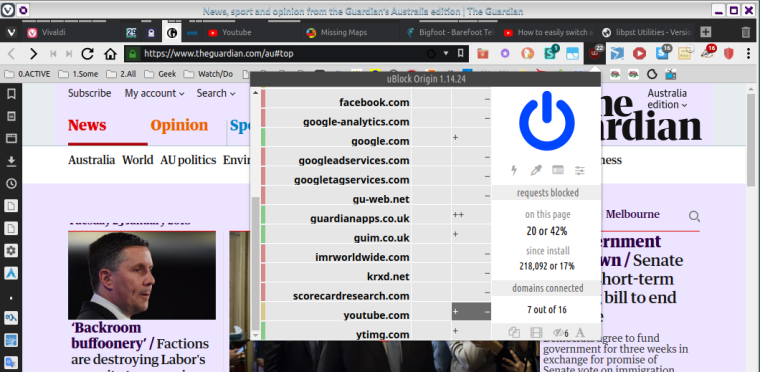
Guardian [& all my other usual sites so far] are still working well even with this extra protection [once i deduced how to "unbreak" various sites]. However as you can see, i had not thought to experiment with 3rd party resources, Inline scripts, & 1st-party scripts. Having seen that you use 2 of those 3 as well. i'm now wondering if i should extend my experimentation to play with them... including of course then deducing how to fix all the sites that would probably break initially.
Tbh i do not understand any of that jargon [per italics above], so grasping the benefits & downsides is tricky for me. Still, no worries, with the kind help here i've already learned a lot of handy new stuff, so maybe a bit more dabbling also might be ok.
-
Thanks for your praise

@steffie said in Canvas Defender, uBlock Origin: General page protection.:
However as you can see, i had not thought to experiment with 3rd party resources, Inline scripts, & 1st-party scripts. Having seen that you use 2 of those 3 as well. i'm now wondering if i should extend my experimentation to play with them... including of course then deducing how to fix all the sites that would probably break initially.
Sure. At least for learning experience, play around with the different settings all you like. You'll never be off worse than before using them at all

I would recommend setting "3rd party" to "globally deny" though (this is what I called 3rd party resources in my text). Be aware that this will probably break some sites initially, but now you know how to get them working again

Tbh i do not understand any of that jargon [per italics above], so grasping the benefits & downsides is tricky for me. Still, no worries, with the kind help here i've already learned a lot of handy new stuff, so maybe a bit more dabbling also might be ok.
3rd party generally means that the (website / javascript / stylesheet / image / whatever) is not hosted on our active site (theguardian.com), but on some other server (e.g. googleanalytics.com) and therefore not under direct control of "your" website. This doesn't mean that it might be malicious per se - but it might mean that you don't need it. So try disabling it and see what happens.
The point is not to allow anything and forbid what is written in some list, but forbidding everything and only allowing what you want/need. Most ad-/tracking resources will be disabled by this method without any list subscriptions anyway.
For completion:
- 1st party scripts are javascript files hosted by the current website itself (here: only those on theguardian.com). The loading of these files can be denied by setting this item to red.
- inline scripts are javascript items, which are delivered as part of the current website HTML file. They are loaded from the webserver in any case, so you can't stop getting them - with the appropriate setting you can disable them. Often these are used for menu effects, selection boxes or - sometimes - for image loading. Often as not the page works well without these.
I might try putting this in an image, but knowing my abilities...

-
Hello. I've continued using Canvas Defender, & monitoring it. It seems to live up to its claim of changing the fingerprint at my specified intervals, as verified with https://browserleaks.com/canvas. In parallel with this i have continued to actively experiment with & greatly expand my finessing of uBlock Origin, although i think now i'll restrict any further posts on that to @Morg42's branched https://forum.vivaldi.net/topic/23893/external-js-resources-and-a-guide-to-safer-browsing.
My next CD query is this: i'd appreciate any interested users posting below with their views on ideal usage of the timer setting. Pls regale me with pros & cons of longer vs shorter change intervals. The Comments on its Dev's Chrome Webstore site span the gamut, which i find confusing. Ta.
-
I don't see any real downsides on short intervals. It doesn't take up constant CPU load and (up til now) didn't actively interfere with browsing experience (in contrast to User Agent changers, which can totally ruin your sessions...)
If you stay on one site (not page), it might not matter; if you change/jump frequently, I'd just dial it down to the minimum of 1 minute and be done with it.
-
@morg42 Many thanks

-
@steffie
What sites did you use test the fingerprinting? I used Panopticlick a long while back and it looks like they have updated their site. If your 'fingerprint' keeps changing, you're going to be unique all the time in the panopticlick test.From what I know canvas fingerprinting only uses the Webgl apiand there are other ways of fingerprinting as you can see from the panopticlick list.
I used to use noscript with FF to block js but it took some effort whitelisting all my usual sites and I felt it was just to annoying having to whitelist each new site I was browsing.What I do now is keep several browsers installed, so I worry less about fingerprinting/tracking. Portable installs are useful for this.
-
@aviv https://browserleaks.com/canvas, which indeed says i'm unique [oh blush, what a special precious petal me, mum would be so proud!]:
Uniqueness 100% (0 of 238238 user agents have the same signature)Initially i thought this was terrible, but then i realised... if my HTML5 Canvas Fingerprint keeps changing [which it does, currently every 5'], & if it never repeats [for which i have to trust the efficacy of this extension; i realise that's a potential Achilles heel], then yes, for each 5' block i'm unique, but over time i'm not trackable, as the fingerprint has no cumulative long-term history that [i thought] was the basis of trackability. Is my thinking wrong on this?
-
purgatori, what do you mean by "beat the test"?
If you want to get a low uniqueness to "blend in", this is one approach.
The extension enables another (as Steffie mentioned) - be unique, but be differently unique every 5 or even 1 minute. Sure, they can identify unique, but what does it help them if they have 30 unique IDs from you for 1/2 hour of surfing? (and new unique IDs the next time you visit the site).Flooding them with useless info can be quite as efficacious as (try and) denying them any information...

